Hello,
I run into an issue when placing an AKS cluster behind a BASIC Azure Firewall.
I am basically following this guide: https://learn.microsoft.com/en-us/azure/aks/limit-egress-traffic?tabs=aks-with-system-assigned-identities (with the exception where I use a basic firewall).
My firewall route table looks like this: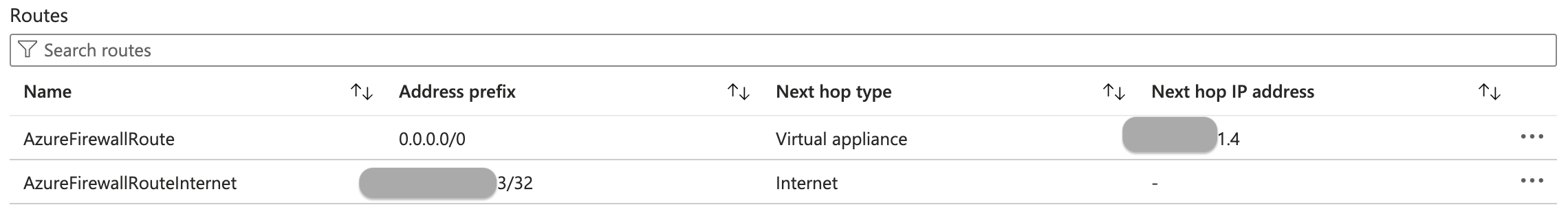
Firewall policy contains following application rules:
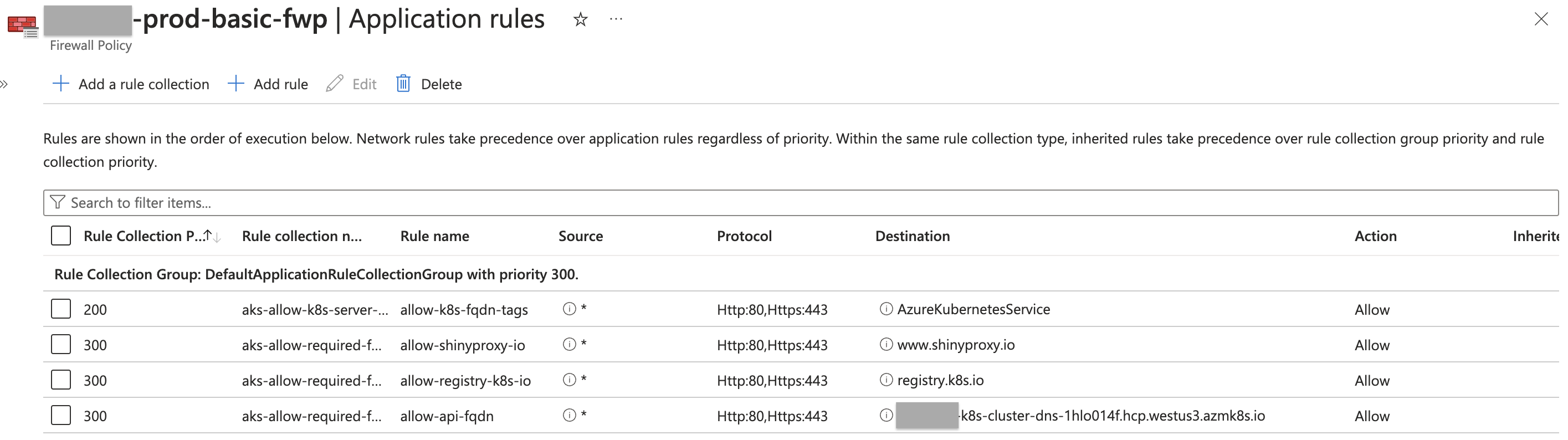
Then DNAT rules to forward ingress traffic through the Firewall’s public IP.
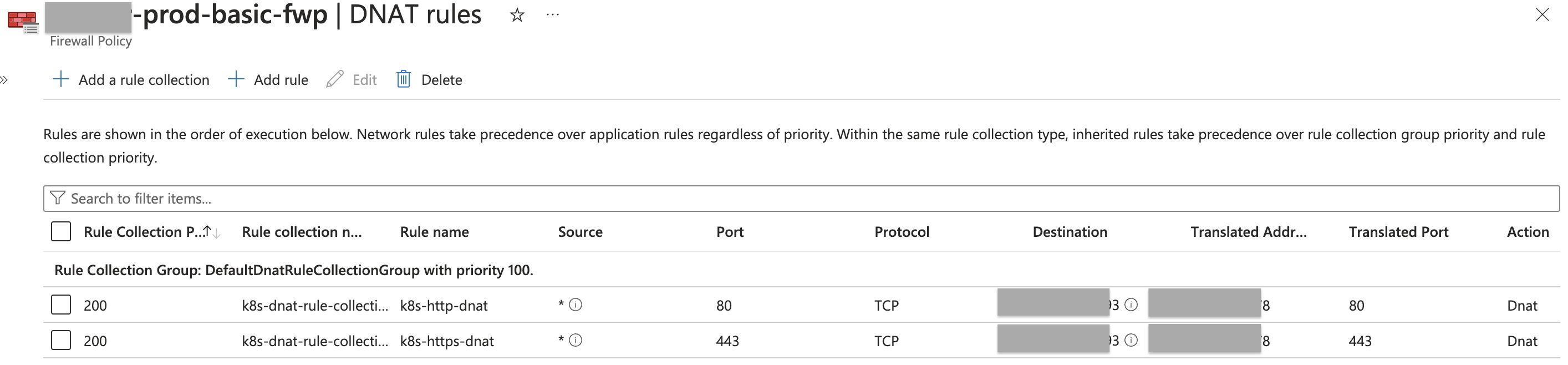
When I try deploying the cluster into a subnet that has the Firewall RT associated nothing seems to work. Pods get stuck in a “Pending” state. I am using the Azure CNI network type and Calico network policy. One observation I made was that in this case pods do not get the IP assignment based on the subnet. As an example, when I deploy the cluster without the Firewall services get IP assignment with no issues (see the following image). But, with Firewall I get a "-" for Endpoint.
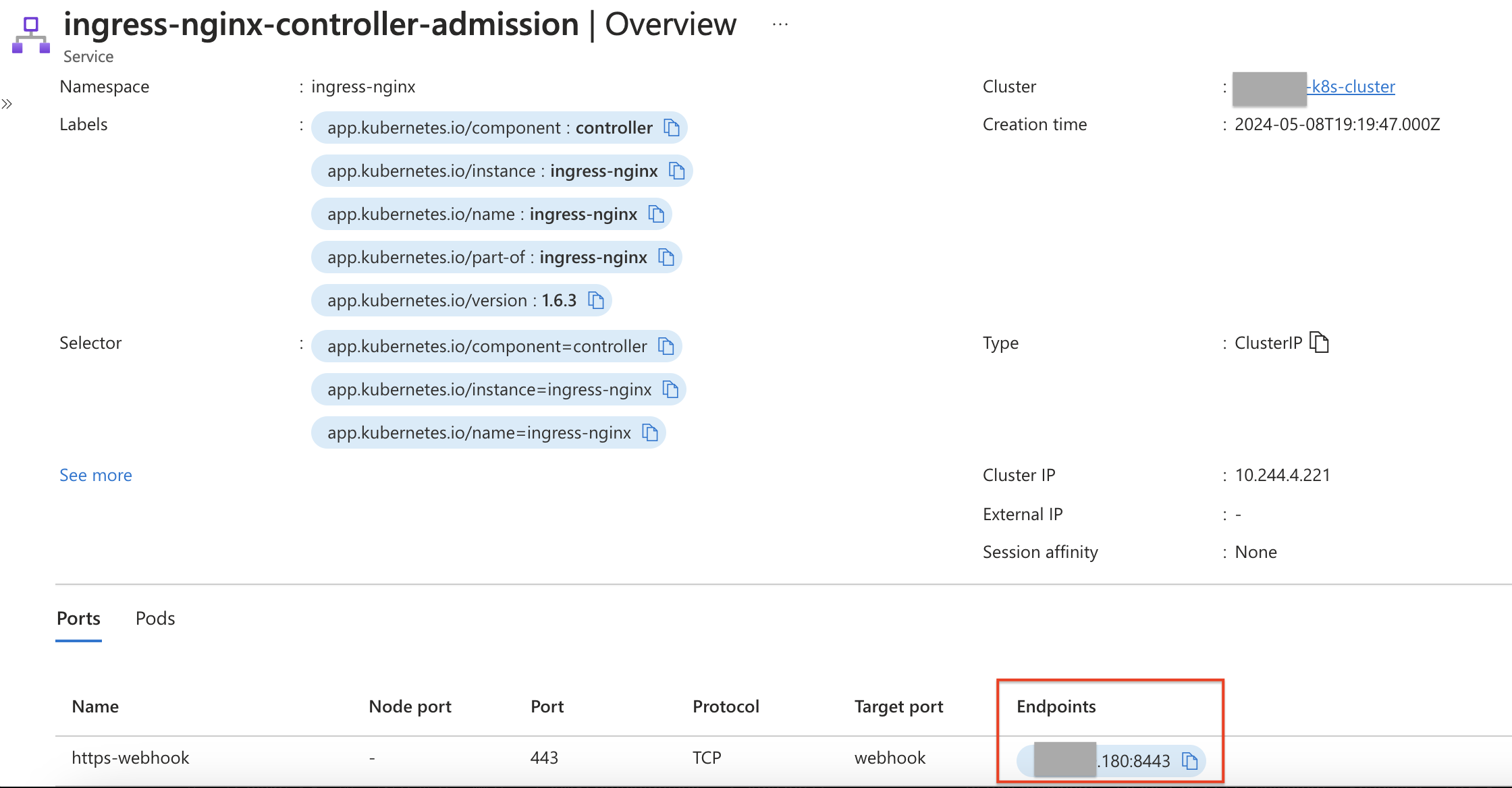
Can someone point me to where the issue can be?
Thank you.
